I’ve found that this topic is quite an undocumented one online and lots of assumptions tend to be made. The majority of content online under this topic that I’ve come across tends to direct you down the route of HA Proxy, which can be fine with very specific setups. But, the minute you want to start to do anything more complex than the basics, HA Proxy soon becomes limiting.
Many websites these days have multiple ports open for specific use cases. Take for example one of the most common web hosting platforms cPanel, this requires many open inbound ports at the firewall layer and in other scenarios we want to give the control to the virtual machine’s operating system the power to decide what ports to allow in without having to configure the firewall every time since they may not have access to the firewall.
We did a blog post recently for How to Setup HA Proxy on pfSense to Host Multiple Websites, which is worth a read to understand the differences for what we are going to cover off here. The core difference here is that with HA Proxy, you have to be explicit when configuring it which ties the settings against a single port, which often is too limiting for many applications.
To get the maximum flexibility you need multiple public IP addresses. This allows you to configure things in any way that you require. So this is what we’re going to cover off in this blog post.
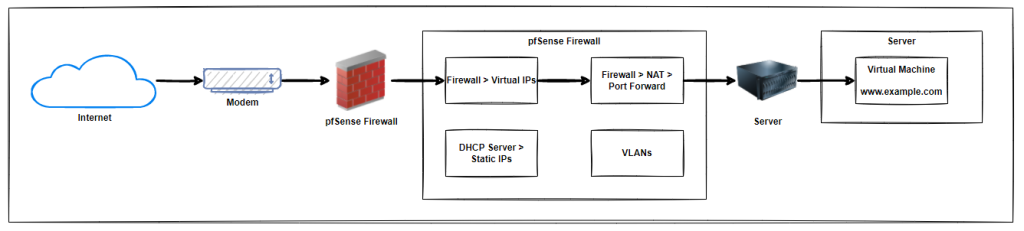
System Architecture
To get a high level view of a setup like this we have the basic components that are outlined below. With a modem, connected to a pfSense firewall which has virtual IP addresses, port forwarding, static IP addresses for virtual machines, VLANs for security configured, then connected to a server with a virtual machine running on it.
In reality, there are often a few bits more along the way and significantly more complex in real world environments, but fundamentally, this is the basic architecture for how all this plugs together.
Purchase Additional Public IP Addresses from your ISP
Firstly, you need to purchase a block of IP addresses from your internet provider. What happens when you do this is that any traffic from those public IP address ranges will ultimately route through to your pfSense firewall so you can then determine what happens to that traffic next.
We’ve covered off a blog post a while ago which helps you to Understand Network Private Address Ranges and looks at the difference between public IP address ranges and private IP address ranges. So take a look at that blog post if you aren’t sure of the difference.
Ok, so now you’ve got your additional public IP addresses.
pfSense Firewall Virtual IP Address Configuration
Now it’s time to tell your pfSense firewall about these IP addresses so it knows how to handle the traffic that is coming in. The first step is to setup Virtual IP addresses within pfSense. To do this, simple navigate to Firewall > Virtual IPs.
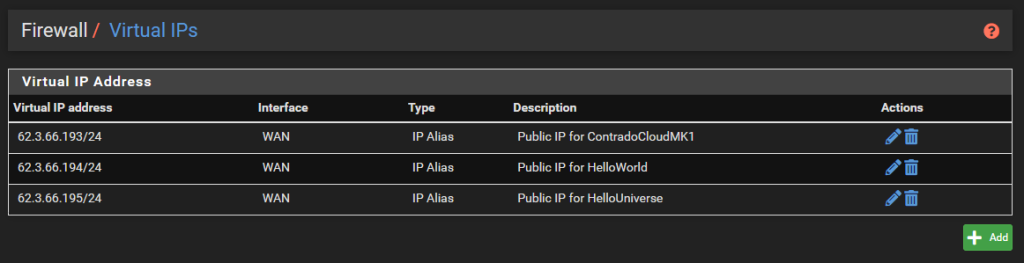
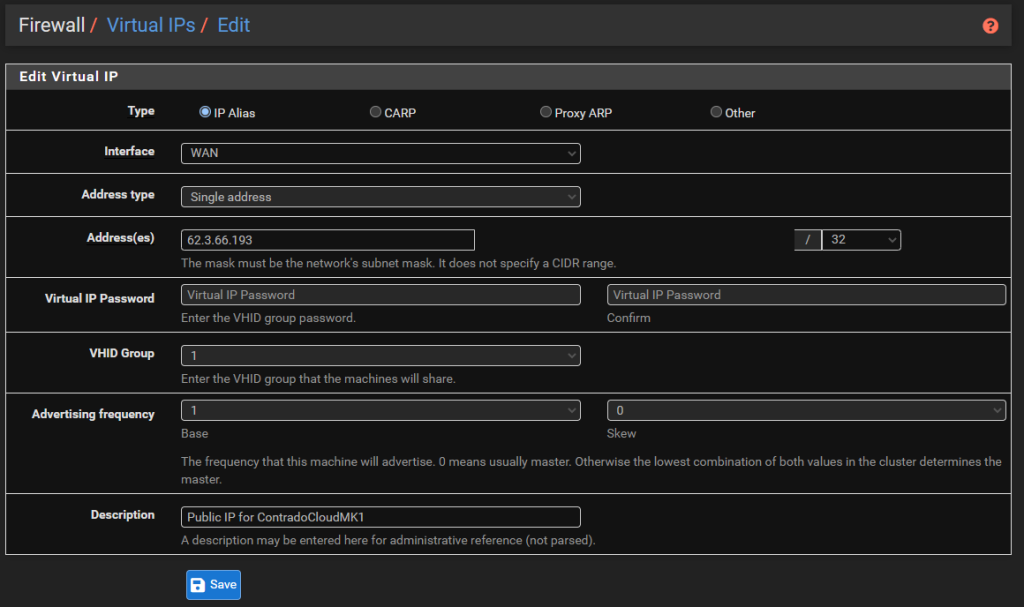
There is nothing particularly complex for settings these up. Simple setup the type as an IP Alias, the interface would be the WAN, the Addresses would be one of the IP addresses with the /32 CIDR range (aka. single IP address), then give it a friendly name and you’re done.
Configure NAT Port Forwarding Rules in pfSense
Now that we’ve got the Virtual IPs configured, it’s time to configure the port forwarding rules so the traffic gets to where it needs to for that public IP address. To get started with this, simply navigate to Firewall > NAT > Port Forward. Then add in some rules.
As you can see in the screenshot below, the settings are rather basic, with the rule being applied to the WAN interface, for the TCP protocol where the Destination Address is the Public IP Address that you added as a Virtual IP Address previously, then forwarding traffic to the static IP address of the virtual machine whenever traffic is received on any port.
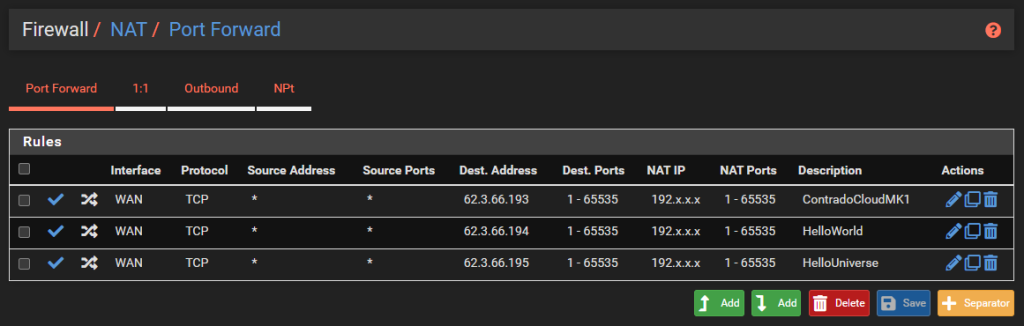
When you do this, pfSense will automatically add a Firewall Rule on the WAN interface.
pfSense Static IPs and VLANs
We’re not going to cover this off within this blog post as this is a separate topic and one that is going to be dependent on your specific setup. The static IP addresses are important to ensure your Virtual Machines always get the same IP address every time they are rebooted so that the firewall rules are still accurate.
Likewise, the VLANs and IP ranges are extremely important from a security perspective to ensure that any inbound traffic is securely segmented from your sensitive internal systems and/or other separate public IP ranges that need to be kept separate from other ones.
Server and Virtual Machines
To keep this bit relatively short and simple, if you have configured all of the above correctly, the traffic that comes into your WAN from specific IP addresses then this will flow through to your virtual machine that you have setup.
So for example, if you have the DNS A Record setup for mk1.contrado.cloud as 62.3.66.193, then this traffic will reach the specific virtual machine where the operating system firewall will then control what traffic it will accept in and what traffic it will deny.
This setup gives you the complete control of the traffic without having to continually play with the pfSense firewall rules.
Summary
Hopefully the above is a handy guide for how to configure pfSense with multiple public IP addresses then use NAT so that you can host multiple websites using multiple ports with minimal configuration within the pfSense firewall.
This is a complex topic, and one that is going to be very different in every single use case. Hopefully this blog post had helped fill in a few gaps in knowledge to get you pointed in the right direction.
Michael Cropper
Latest posts by Michael Cropper (see all)
- WGET for Windows - April 10, 2025
- How to Setup Your Local Development Environment for Java Using Apache NetBeans and Apache Tomcat - December 1, 2023
- MySQL Recursive Queries – MySQL While Loops – Fill Zero Sum Dates Between Dates - October 6, 2023

Hi, in my scenario i have an FTTH direcly connected to Pfsense’ s ethernet with provider’s VLAN and PPPoe.
In my case, this config does not work.
Do you think it depend from provider?
Sounds like that should be fine. I’m UK based and previously I had FTTC, so needed: Phone Line –> RJ11 Cable –> Modem –> RJ45 Cable –> pfSense Physical Firewall/Router. My ISP uses PPPoE, and I simply configured the Modem in Bridge Mode, then added my ISP credentials to pfSense and all worked fine.
I’ve since upgraded to FTTP/FTTH, and currently using a temp router/firewall as I’ve not got around to getting pfSense set up yet. Only difference I’ve noticed with FTTP though is that it looks like you don’t need a modem any more as the optic cable goes into a box which outputs a standard RJ45 cable, so that can then go straight into pfSense/any other router.
What is the issue you’re getting?
The advantage is that the configuration without modem eliminates the double nat problem and the public interface of the firewall corresponds to the public ip address issued by the provider.
The problem is that I still haven’t figured out how to correctly add the new subnet from 8 ip addresses. I’m groping in the dark. Got an idea?
So you have purchased a block of 8x Public IP Addresses from your ISP then. Of these, you can only use 5 of them as actual Public IPs for the purpose of NAT – I can’t quite recall off the top of my head why this is, it’s all background stuff that means certain IPs are needed for other stuff between your Firewall and your ISP.
But basically all you need to do is;
1. Interfaces > WAN: Add in your PPPoE Username and Password so you can connect to the internet
2. Firewall > Virtual IPs: Add one of the five available IPs from the block of 8 as an IP Alias against the WAN Interface using the 1.2.3.4/24 notation
3. Firewall > NAT > Port Forward: Setup to point through to the internal IP you want to send the traffic to
Bearing in mind that you need to make sure that final internal IP is allowing traffic inbound and isn’t getting blocked by any kind of firewall at that point.
Which bit isn’t working for you?
Hi, I found out that it depends on the phone provider.
On one of the two available data lines, I simply configured the NAT using one of the public ip’s to an ip on dmz and it works without any other additional configuration.
Interesting, thanks for sharing findings. I don’t know what’s going on under the hood at UK ISPs, but clearly some cobbled together nonsense, as I’ve circled through many different ISPs and they all seem to operate differently. Not sure if this is a tech challenge, or just stupid business processes, or a mixture of both. Took me a while to find a UK ISP that can offer block of Static IP Addresses to a residential address.