by Michael Cropper | Apr 24, 2016 | Data and Analytics, Digital Marketing |
Sorry, I’m calling it. Businesses purchasing subscriptions to companies that are offering free data at a hugely premium price need to stop paying for this now. Stop wasting your money. Hell, give it all to a charity of your choice, it will be better money spent.
The company I’m talking about, for anyone working in digital will be well aware who this is, but for legal purposes let’s just call them a fictitious name which bears no resemblance to any company or person which happens to have a similar name, EnquiryForensics.
The offer for these types of companies is that you can “See who is looking at your website”. In summary, no you can’t. The only information that these types of companies generally provide is information that someone in Company X was looking at your website, then joining this data together with generic contact details for this company or publically accessible contact information for various staff within this organisation. This does not tell you who specifically is looking at your website. There are a whole host of data protection issues with tracking individual user website usage which is why services like Google Analytics are obliged to anonymise certain aspects of the data.
So beware, any company trying to sell you access to a tool or service which can show you who is looking at your website in a company, it is likely a snake oil salesman or company. You can generally get whatever data that have completely for free, and here’s how.
Google Analytics is Awesome
I’m not going to go into depth about Google Analytics. In summary though, Google Analytics tracks over 560 points of data for every website visitor and when you know where to look, you too can start to see how valuable this data is.
Identify the Companies Looking at your Website
Simple. Within Google Analytics, go to the following report: Audience > Technology > Network. This report will show you the companies who have been looking at your website, which can be extremely valuable for any type of B2B business as you can then feed this into your outreach pipeline and support the work your business development manager is doing on a daily basis. Look;
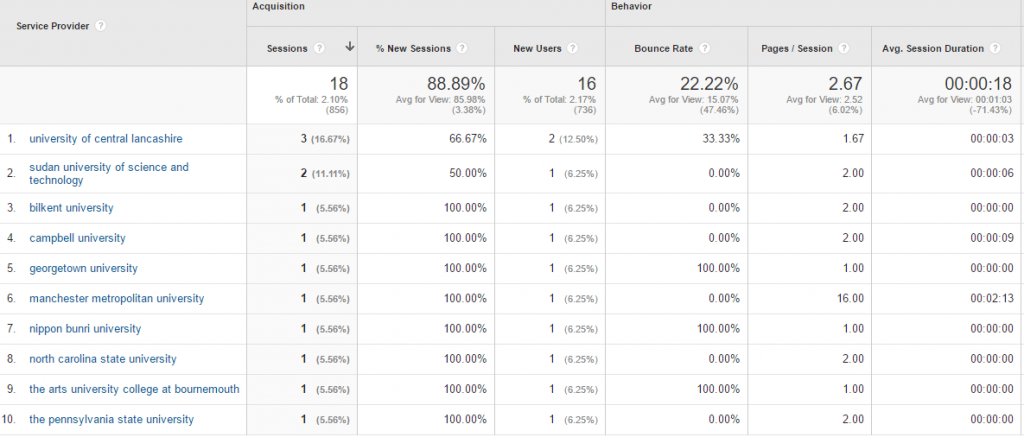
It’s all there. The companies who have been looking at your website which you can filter through to your hearts contempt. For any companies listed within here which are SMEs, a quick Google search for the company name and check on LinkedIn will soon allow you to identify the relevant person to speak with in the company who could be interested in your products and services.
Even better, you can then begin to filter down by looking at these individual companies and see what pages they viewed on your website too, so that you get a better understanding of what they are looking for.
The key here is not to be too creepy though when you reach out to these people.
All in all, you rarely ever need to pay for premium services and tools which allow you to identify who is looking at your website. With a bit of know-how, you can have access to all of this type of information for free.
If you want to find out how Google Analytics can help your business, get in touch.
by Michael Cropper | Apr 13, 2016 | Data and Analytics, Digital Marketing |
Blogging is a core part of any digital marketing strategy which is why we talk about this on a regular basis to businesses. We’ve already produced a Really Simple Guide to Blogging, so have a read of that resource once you have finished reading this blog post.
We get asked a lot about how important is blogging, really? Well I thought it was worth putting a few numbers behind this to put this into perspective about why we talk about this so much;
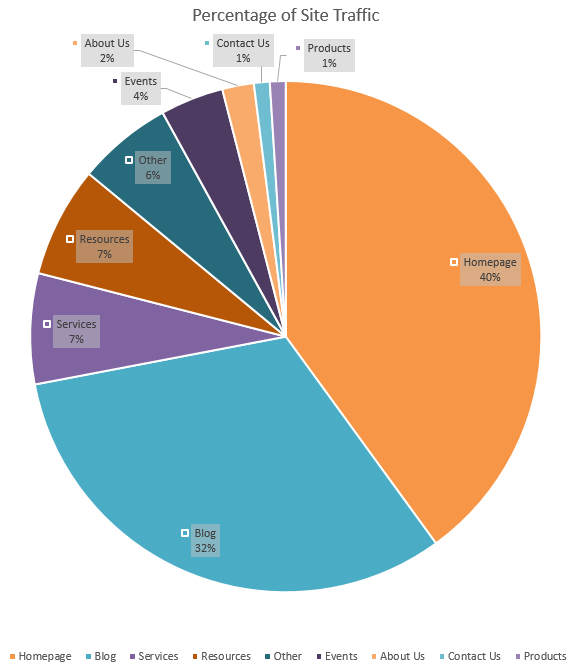
As you can see from the data above from our own website, when looking at the Blog and Resource pages which drive traffic to the website, this accounts for almost 40% of website traffic. Now to put this into perspective, imagine if you currently aren’t blogging on a regular basis. You are missing out on an enormous amount of traffic to your website. Assuming you aren’t blogging, by starting blogging based on these figures you could grow traffic to your website by almost 70%, imagine a 70% growth in traffic to your website. Pretty awesome, right?
Sure, things are a little more complex than this in the real world and for ecommerce websites this split is likely to be significantly different, but hopefully this gives you a few figures to highlight the importance of blogging. Get in touch if you would like to talk to us about how blogging can help boost your digital strategy.
by Michael Cropper | Sep 19, 2015 | Data and Analytics, Developer |
To put things into perspective, let’s look at the handy tools we have on our personal computers for monitoring computer resource usage. If you’re on a PC then you can easily view the Performance data within your Task Manager and I’m sure there is something similar for you Mac users out there;
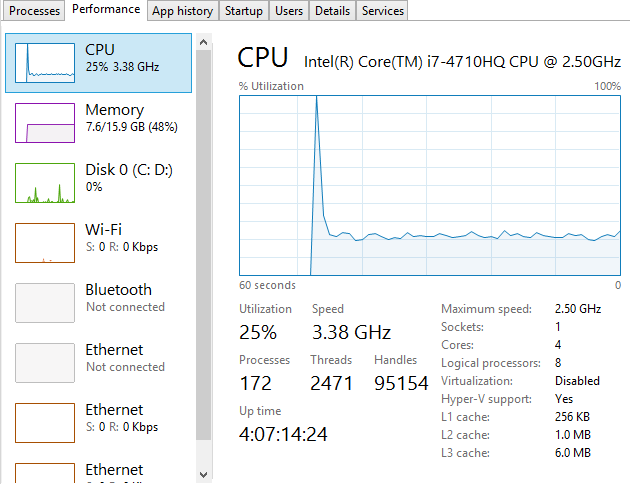
This is a very handy little tool which clearly shows you how your personal computer is performing and how things perform when you start to open new applications such as Microsoft Word or the memory eating Google Chrome browser. Here’s what happens when you kill Google Chrome after you have closed the application;
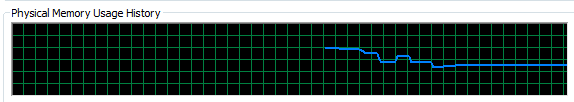
Interesting to say the least…
Anyhow, the point here is that monitoring the performance of your personal computer is relatively simple if you know where to look. Now we’re going to look at how to monitor your web server resources accurately using a suite of tools and also look at the significant differences between how different tools report on how many resources have been used and how many are free to use. The differences are what we are going to be focusing on as they are huge and can lead you to believe that you actually have more resources available than you really do.
Web Server Resources
Before we jump into monitoring your web server resources, let’s just define this. Essentially the key resources related to your web server include;
- CPU – The quantity of CPUs and their processing power in total.
- RAM – The quantity of memory currently in use and free for other things. Plus the quantity of RAM reserved for buffering and caching.
- Hard Disk Drive Space – The number of GBs of data you are using compared to the size of your disk.
- Disk I/O Utilisation – The number of input/output connections to the hard drive per minute which again has a limit
- Network I/O Utilisation – The amount of traffic on your physical network infrastructure
Behind all of these key metrics includes an enormous amount of information about the software that is running on the hardware and which processes are hogging these physical resources. This is where web server monitoring software comes in to its own as this can provide you with some extremely powerful data about how your web server is performing and most importantly, when you need to look at upgrading your web server to cope with the demands of the website or websites that are hosted on the web server.
Just as with your personal computer, web servers have a limit which needs to be managed effectively. If you tried to open 1000 Google Chrome browser tabs, your computer would probably grind to a halt as the physical hardware resources would be pushed over their limit. To the point where you would probably have to reboot your computer to resolve the problem. Your web server is no different, it’s just a little more complex, doesn’t have a physical button you can turn it on/off with (or kick!) and is sat in a huge data centre somewhere, ours are in Manchester & London.
When running a web server, it is clearly a little more important than your personal computer as this contains your website, the digital front of your business which is why it is essential to do everything physically possible to work towards a near 100% up-time. I’ll not cover today about why a 100% up-time is impossible to achieve and any guarantees of this are a flight of fancy, instead today we’re going to look at how to monitor your web server resources accurately using a suite of tools, specifically New Relic and Munin.
New Relic
We use New Relic on our web servers because it is extremely user friendly (well it is for someone of a technical nature compared to the other tools we have to work with). Being able to easily graph server resource usage to the n’th degree.
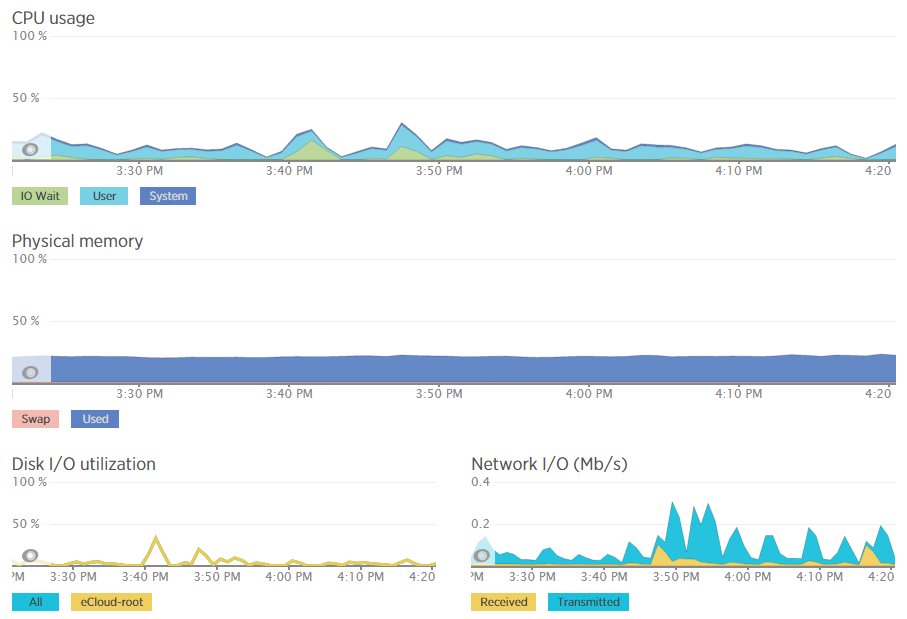
Which then further breaks this data down into the different processes that are using the resources, which websites hosted on the server are using the resources and also which user accounts are using the most resources and so on. Going beyond this, New Relic also allows us to monitor the up-time of our servers which is extremely useful for us to continually improve the performance of our servers over time;
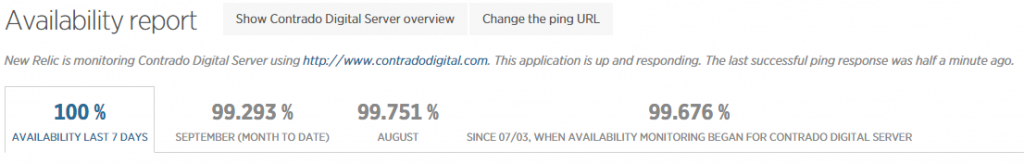
As mentioned previously, a 100% up-time is almost impossible to achieve due to various reasons which we’ll cover in another blog post. As you can see in August and September, the server has been performing exceptionally well overall but has had a couple of blips which we’ve worked to improve performance following this. The important aspect here is that we are tracking this data which means that we are capable of acting on these insights we have to continually improve the service to our customers. We already use industry leading server technology which can always be improved further by actively monitoring performance and improving areas which need attention.
What is interesting with the New Relic data though is that the memory usage data isn’t quite as accurate as it seems on first glance which is due to the way Linux organises data at the operating system level to improve performance. By default, Linux see’s RAM as wasted space if it isn’t used so it looks to utilise the available RAM to speed up performance. This is great in theory, although can cause a few issues if not carefully managed. Accessing data from RAM is up to 1000 times faster than accessing the same data from a hard drive which is why RAM is such a powerful way to increase the performance of technologies and hence make your website load faster. It’s a shame that it’s so expensive to purchase in comparison. I guess we’ll just have to wait for the next wave of hardware innovations to break through this barrier. Specifically related to server management and New Relic, the underlying way Linux classifies available RAM compared to how New Relic reports on this data isn’t quite accurate which can be misleading.
For example, when analysing one of the blips we had recently, at either side of the troublesome time, server resources within New Relic were being reported at well below 30% usage for CPU and well below 40% usage for RAM;
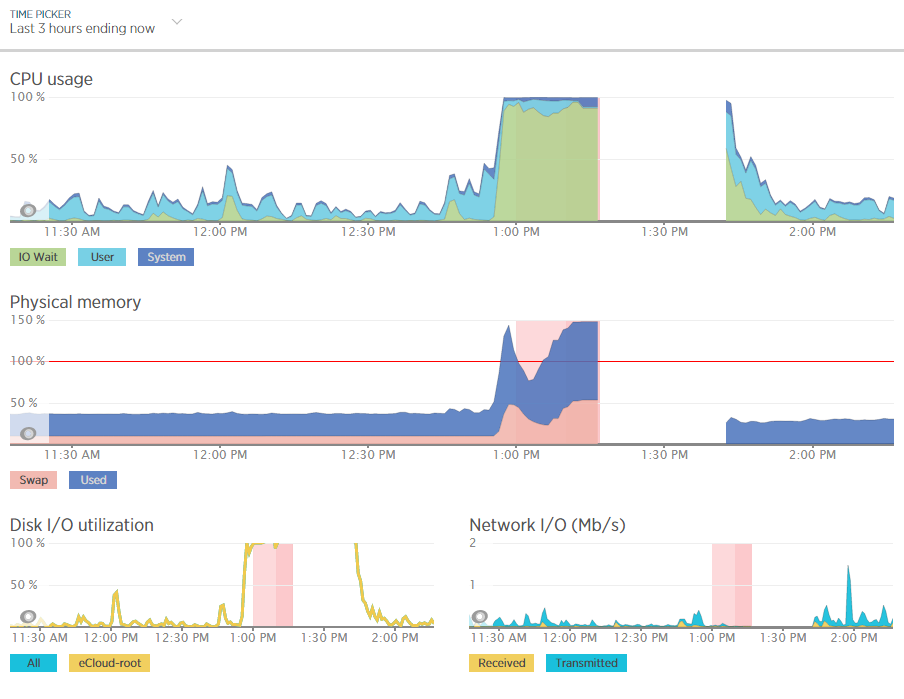
Although the blip happened for a specific reason which we needed to get to the bottom of this so we could prevent this happening again. Thankfully we have multiple tools at our disposal which allowed us to fully investigate the issue and take the necessary steps.
Using external tools is a great way of reporting on performance although they are external from the system and they may be reporting on data in a slightly different way. So we investigated this going back to the command line interface and logging into the server via SSH & PuTTY to query the server directly to get some more accurate information. What we found was rather interesting. When querying the server directly to see how much memory was being used this highlighted that the performance data within New Relic was actually quite a way off when it comes to its accuracy;
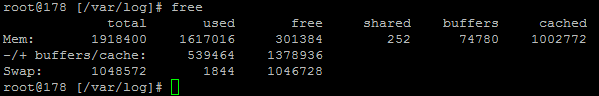
Here we see that there is only 300MB of RAM free out of 2GB opposed to the 60% free which equates to around 4x this figure at 1.2GB which is being reported in New Relic. Quite a difference here. The difference relates to the Buffer / Cache data which is being used by Linux to speed up the web server yet isn’t being taken into account by New Relic. While this is a nice setup to have, this does have its own performance issues when spikes occur which can lead to problems as outlined earlier.
Doing a one-off report for server resource usage via the command line is nice, but it is only a snapshot so doesn’t report on the true performance of the server over time. Thankfully we use another web server monitoring tool called Munin which essentially does a similar thing and much more then graphs all of this data over time.
Munin
Here is where the open source technology Munin comes in. Good old open source projects providing more insight than enterprise level software yet again. This is not a dig at New Relic as this software is really good, more of another stripe on the open source community for being so awesome.
Munin is designed to report on how your web server is performing in a similar (but not as pretty) way as New Relic. When looking at the same data within Munin as what we were looking at within New Relic the data was clear to identify what caused the issue;
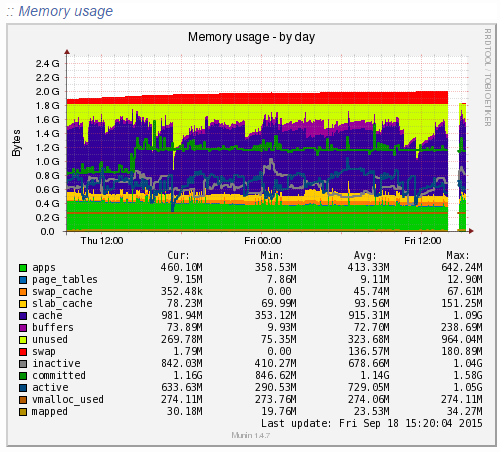
Ok, clear to me… What the above graph is showing can be summarised as;
- Red: This is the memory swap data which is outlined in more detail below. Importantly, this memory swap data is also highlighted on the New Relic graphs.
- Yellow: This is the available RAM
- Purple: This is the cached data sitting within the RAM. From New Relic’s point, this is available RAM, although from a physical hardware point, if we want to access this space we first have to clean something out, retrieve the data from the hard drive then add the data back in to RAM which consumes a large amount of processing power on the CPU
- Green: This is the memory taken from the applications in use on the web server
Note on the Red data in the graph above, the Memory Swap. What is actually happening here is that Linux is deciding what files to move in and out of memory based on what it thinks are the most important files. This work takes up valuable resources which is why the CPU levels and the Disk I/O levels on the New Relic graphs above spike right when this hits its peak. This is essentially the web server scrambling to optimise the performance at the detriment of its overall health. It’s the same as when you push yourself physically too much and then become ill from the process and need a rest. It’s the web server doing the same thing. When you start to see an increase or a significant amount of memory swap data within your New Relic graphs, I’d recommend checking to see what is really happening at the server level as this essentially highlights that your web server needs a bit more RAM or that you need to optimise the way Linux utilises the memory;
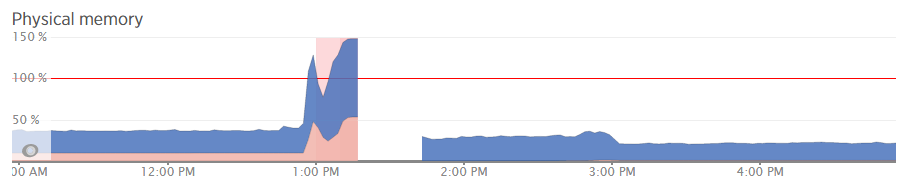
What all of this highlighted is that we needed to notch up the RAM on this server a bit. The aim was to increase the available RAM to allow for a greater amount of unused RAM meaning that the CPU nor the hard drive wouldn’t have to work as hard to access the information needed. As you can see, when we increased the RAM around 3pm in the above graph, the memory usage percentage went down within New Relic. As we know though, the New Relic data isn’t 100% accurate, so looking at the Munin data this highlights how we are now in a situation with this web server which means that the resource intensive memory swapping (the red bit on the graph) is minimal, there is more available RAM (yellow) and Linux has decided it wants to increase the cache so the websites load even faster than before;
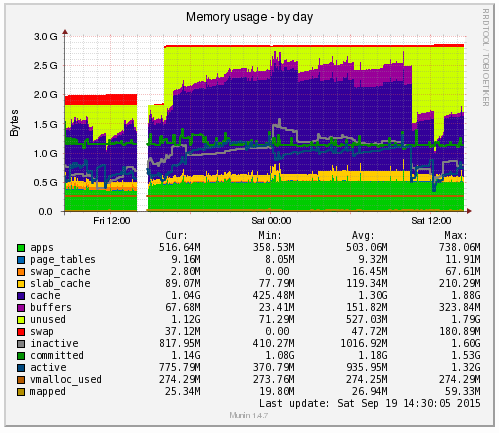
Likewise when looking at the memory usage via SSH;
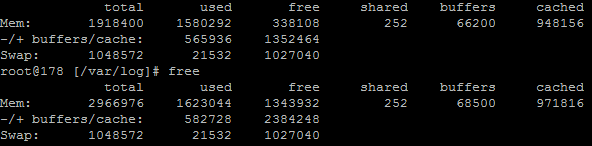
This again echoes the Munin data. The above data is in kBs, showing around 1.3GB of free RAM opposed to 300MB previously.
Summary
What is extremely simple to achieve on your personal computer is a little more challenging to setup, implement and report on for your web server. Web server management is an extremely specialised field which is why we only use the best technology with a dedicated team of server engineers behind the scenes to ensure that we are continually improving the performance of our web servers. All of this is to work towards the constant goal of 100% up-time for your business websites.
Not all web hosting is the same and not all web hosting companies work in the same way. Speaking for ourselves, we take web hosting seriously. A web server is not just a computer that sits in the corner somewhere which hosts your website. A web server is the cornerstone of your digital storefront which is why we invest heavily by utilising leading technologies allowing us to continually improve our services for all our web hosting customers.
As a take away from this post. If you’re a non-technical person looking for web hosting, you can guarantee that we’re ‘on it’ when it comes to hosting. If you’re a technical person reading this, then the top tip is to use multiple web server resource monitoring packages to provide a full insight into performance as some tools aren’t as accurate as they may seem on first glance.
by Michael Cropper | Jun 18, 2015 | Data and Analytics, News, Security, Tracking |
Did you know that Google is tracking your every single move? No? Most people don’t, yet they are;
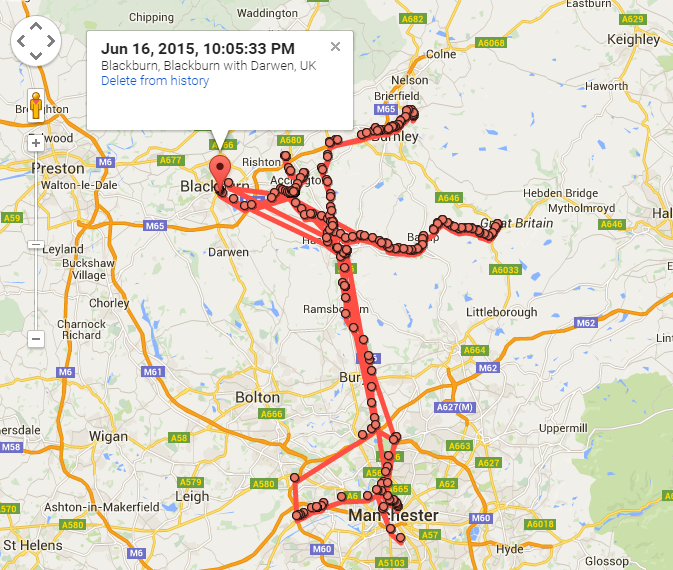
The above is where I have personally been recently while out and about on the road visiting businesses which is naturally a large part of the work that I do. This isn’t some feature that I have personally set up. No, this is something which Google has enabled by default and means that they are tracking my every move, and yours too. I’m sure there will be some small print in the terms of use somewhere but this isn’t the point.
Google is not alone in this activity. Back in 2012, Apple were found out to be tracking users without permission. With the rise of smart technology such as phones and tablets, which have many sensing devices built in, there needs to be a much easier way for users to understand what data is being tracked and how this is being used.
Check what Google knows about where you have been recently
To see what Google knows about where you have been recently, click the above link and sign into the (or one of the..) Google Accounts that you are signed into on your mobile phone. You’ll be surprised at what you can see!
Clear Permissions and User Control
Currently it is not clear for users what data is being tracked by the majority of software and apps that you are using on your mobile devices. The industry as a whole needs to take more responsibility for privacy and security related issues. Google has recently launched Google My Account which is designed to take this a step closer to where we need to be, although I’m not sure this going far enough;
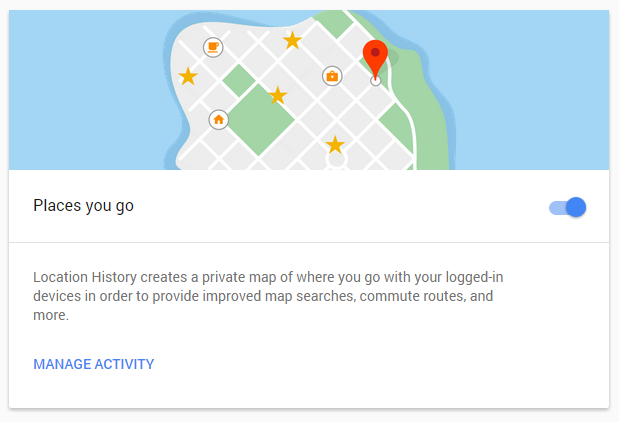
If you are concerned about what information Google is tracking about you, it would be recommended to check through the settings for all of your Google Accounts within the My Account feature that has recently launched. Specifically where you can turn off the feature for how Google is tracking your every move if you feel this is a little too invasive into your life. Simply navigate to the Personal Info & Privacy page, then scroll down to the Places You Go section to turn this off;
Privacy
The amount of data that is being collected about everyone on a daily basis is enormous. Data that can ultimately be used for advertising purposes, sold to other companies or even stolen by cyber criminals. There are already rules in place around data security including the Data Protection Act which states that any information stored must be;
- used fairly and lawfully
- used for limited, specifically stated purposes
- used in a way that is adequate, relevant and not excessive
- accurate
- kept for no longer than is absolutely necessary
- handled according to people’s data protection rights
- kept safe and secure
- not transferred outside the UK without adequate protection
There is stronger legal protection for more sensitive information, such as:
- ethnic background
- political opinions
- religious beliefs
- health
- sexual health
- criminal records
What is interesting when comparing the above with what is actually happening in the world, it takes no legal expert to raise a few eyebrows at the disparity between the rules and reality. What is clear though is that there needs to be a much more thorough and clear process in place for all data stored about people by large organisations. When comparing this to a real world context, if you were being followed around all day, every day, by a private investigator how would you feel?
by Michael Cropper | Jan 25, 2015 | Data and Analytics, Developer, Tracking |
We have been seeing a large rise in referrer spam in Google Analytics which is causing problems for a lot of website owners. There is also a lot of misinformation on the web about how to resolve these issues which we will look to clear up in the blog post and the subsequent resources we have created to block spam bots in Google Analytics. This blog post will look at what causes referral spam in Google Analytics.

What is a Referrer
A referrer is a HTTP Header that is sent to a website when a user clicks on a link from one website to another. For example, within your web analytics software such as Google Analytics, you can see what other websites (the referrer) are driving traffic to your website which can be useful to track how popular your website content it around the web.
The referrer is extremely valuable although due to its nature, it is possible to abuse this information and trick web analytics software into thinking a genuine user has performed an action on an external website to visit your website. When in fact this was just completed by a software script to mess with your analytics data, often to place links into your web analytics platform designed to make users take a look at those which can often be a virus or an affiliate link to a popular website so that they can earn money the next time you purchase something from that website.
How Referrer Spam Works
It depends. Referrer spam comes in two main forms, particularly when related to Google Analytics. Sometimes the script will actually visit your website and execute the JavaScript files for Google Analytics, which then sends the data into Google Analytics. Whereas other times data is just sent directly into Google Analytics without the script ever visiting your website. Depending on what is happening within your own analytics software will depend on how you deal with the spam and remove it.
What actually happens with all types of referral spam is that the HTTP Referrer header information is faked. When creating scripts to spam people, to explain this simply, you say what the URL is and what the HTTP Referrer header information is. For example;
URL: www.contradodigital.com
HTTP Referrer: www.another-website.com
So when Google Analytics receives this information, the www.another-website.com shows as a referral website visit which is why it then appears within the Google Analytics reports. The finer details are a little more complex than this in the background, but this gives you a basic understanding of what is happening.
Referral Spam that Visits your Website
One way referral spam gets into your Google Analytics reports is when a spam bot actually visits your website and loads the Google Analytics JavaScript.

From Google’s point of view, the data that has been received for the HTTP Referrer is genuine and there is no way of determining any difference. Hence why this data is sent straight into Google Analytics just like a valid website visitor’s data would be sent into Google Analytics.
This type of referrer spam is actually reasonably simple to block using the .htaccess file. Read up on the finer details on the resources page about how to stop this. Essentially, you can block certain website visits if they have come from a certain source. For example, you could block anyone trying to access your website if they have come from www.google.com. But you wouldn’t do that, that would be insane. Instead, you can identify the spam domains and block access from these.
Referral Spam that Sends Data Directly into Google Analytics
Other types of referral spam will send data directly into your Google Analytics account without ever visiting your website. Which makes dealing with this type of referral spam a little different. How this actually works is that a script sends the data directly to Google Analytics and associates this with your account. Your account has an ID number which looks like, UA-00000001-1, then another website owner has an account like UA-00000002-1 and so on.
So how these types of scripts work is that they simply send the fake data directly to Google and the different accounts, essentially looping through the account numbers hundreds of thousands of times so their referral spam ends up in as many different accounts as possible. The data that is sent through into Google Analytics by spammers can be customised to whatever they like, which is a little annoying for website owners and a continual job to keep up to date with this.
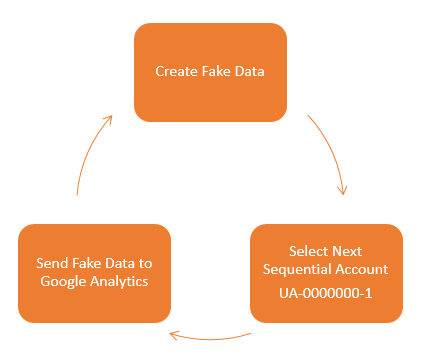
What this means is that you need to take a different approach to block this type of spam from Google Analytics. This needs to be implemented directly within Google Analytics. There are two things that you can do within Google Analytics which are blocking spam bots that Google is aware of and also blocking individual referral domains that aren’t being blocked by default. There is a full guide on how to block this type of referral spam over on our resources page. If you have any specific queries about how to deal with referral spam within your own Google Analytics account then get in touch and we can take a look at what the solution will be for you. If you are interested in reading the highly technical details behind what is happening, then this post explains this in great detail.
by Michael Cropper | Jan 15, 2015 | Data and Analytics, Digital Marketing, Events, PPC, SEO, Social Media, Technical, Tracking |
Just before Xmas I was invited to speak at the Creative Entrepreneur event at Media City in Manchester to share insights into how online retail is changing. In-between speaking, it was great to listen to other online retail experts to hear their thoughts about where things are heading. So we can take a look through some of the discussions points in this blog post.

ASDA
First up we heard from Dom Burch, the serial speaker and senior director or marketing innovation and new revenue at Walmart UK (Asda). He shared his insights into how some of ASDA’s recent campaigns have been hugely successful in many aspects online and offline.
Dom’s first tip was around innovation and the importance of innovating throughout your entire business, regardless of how big or small you are. Innovation is key to long term and sustained growth. Simply dipping a toe in the water isn’t going to cut it here, Dom advised that you need to be giving projects at least 6 months to succeed (or fail!) so that you can be confident that you have exhausted all possibilities for the idea and had the time to gather data and assess the results accurately.
With all innovative ideas, you are starting with a goal of some kind for the business. Starting with ambitions to “become a big business” is equivalent to starting with the idea of “making a video go viral”. It’s simply the wrong approach to take and will inevitably lead to disappointment as goals are not hit. Instead, start with goals that are relevant for your business, goals that are in-line with your customer demands and goals that you can actually influence.
In between these ideas, Dom shared a few interesting statistics about ASDA;
- ASDA FM listeners have more people listening that Radio 1 and Radio 2 combined
- There are over 18 million customers who visit ASDA stores weekly
- ASDA’s website has over 300 million impressions every month
These are quite similar figures to what was announced last year at a digital marketing conference in Manchester.
With ASDA spending over £100 million per annum on broadcasting adverts, Dom’s approach was to get the PR team using Twitter, which was quite a challenge. Spending as little as 2 hours per week on Twitter, the newbie-to-Twitter PR team were already having a conversation with the editor of Vogue within 2 weeks. Where else could you get this kind of conversation going in 2 weeks? It simply wouldn’t be possible.
Another tip came in the form of doing something yourself first so that you know how to do it. This is something that I firmly believe in personally and in business. If you don’t at least understand what is happening, how can you ever hope to really manage this process? This is not to say you need to be an expert in every aspect as this would be impossible. Instead, it is hugely important to get a good grasp on every aspect within business and digital so that you can fully understand why things are being implemented and the reach they will ultimately have.
The simple process above will help you to build fast, fail quickly and innovate throughout your business at speeds you have never done before. Ideas are worthless, implementation is key and the only way to see what does and doesn’t work is to loop through the process as fast as possible, while giving every idea the time and energy to succeed.
Have a think for a moment, what are the 10 ideas that you have been talking about in your business last year? I can guarantee that there will certainly have been more than 10 ideas, but what were the 10 most important ideas? How many of these have you actually implemented, 5, 3, 1, none? Start the year off as you mean to go on. Run through these 10 ideas and measure everything to see how they impact your business. Capture the data and make informed decisions about the success of each campaign or idea.
For established businesses like ASDA, they aim to spend between 1-5% of their marketing budget on what Dom called “Trial and Error” campaigns which may or may not work. For businesses within the SME market, I would suggest this should be much higher as you are often still in the stages of experimenting with campaigns to see what works for your business. We naturally review and manage a lot of campaigns in the day to day work we do, although even we cannot tell you with 100% accuracy what will or won’t work for your individual business. We can certainly take into account the years of expertise and make a highly educated decision, although every business and every customer is different.
ASDA know that 74% of their customers are on Facebook, 20% are on Twitter and 15% of their customers watch YouTube daily. This information allows ASDA to invest their digital marketing spend in the right areas and not simply spend money on ‘more followers’ with no engagements. Their YouTube strategy focuses on how-to style videos and researching products which are broken down into 3 main groups;
- Hygiene content: Something that is core to what you do and for your core target market
- Hub content: Regularly created content designed to push this in front of your audience
- Hero content: Large scale campaigns to raise brand awareness, think about the epic Volvo Trucks campaign
The next of ASDA’s campaigns that was shared was with the involvement of Tanya Burr. Who you ask? Ask your teenage daughter if you have one. If you don’t, like me, then I also had to Google her to find out a bit more about her! She is described as a “Beauty, Fashion, Baking, Lifestyle Blogger & YouTuber” in a nutshell. And more than that, she has 1.2 million followers on Twitter. This is the reason ASDA worked with her, to reach this huge audience. The reach that ASDA’s products gained on social media was astronomical, just take a look through the number of views for each video that they produced together and you will start to understand how collaborations like this can pay off. Where else could you gain that kind of reach? To put things into context, Game of Thrones receives around 1.3 million views every week, which is less than what ASDA managed to reach with this collaboration. Likewise, Tanya Burr has more followers on Twitter than Sheryl Cole, Madonna and BBC Radio 1. Just because you have likely never heard of people like Tanya, doesn’t mean that they aren’t hugely successful.
When looking at YouTube videos specifically, always keep an eye out on the engagement levels and not simply the number of views of a video. Any brands that have a lot of views yet very few likes/dislikes means that they have likely paid a lot of money to drive traffic to the YouTube video and no-one liked it so they just bounced straight back out again. High engagement levels allow you to listen directly to your customers in ways like never before. ASDA’s videos with Tanya weren’t simply ‘buy this product’ videos, that’s boring and a fast way to drive customers away. Instead, they focused on food, health and wellness, beauty and style.
ASDA took this whole campaign one step further by creating the Mums Eye View YouTube channel which linked together their partnerships with Tanya Burr, Zoella and the Lean Machines. Google them all to grasp the scale of what is being achieved with strategic partnerships. This is a very young audience that ASDA was targeting here and one that has clearly paid off. With reports of as little as 2p per view of a YouTube video, 70% retention rate, 4 minutes minimum viewing time with an average of 7 minutes in length per video. You could only achieve these results with effective digital marketing that focuses directly on your customers. Not once did ASDA think “let’s make this video go viral”. What this also shows is that people like long form content on the web. No more do videos have to be 2 minutes in length, don’t be afraid of pushing the boundaries to meet customer demands.
This brings us nicely onto newspapers and traditional newspaper advertising. Quite frankly, no-one reads newspapers anymore, and I don’t say that lightly. Ask yourself, when was the last time you bought a newspaper? Personally, I can’t remember the last time I bought one, other than on the occasional times when I’m featured in one to keep as a little memento. Keep everything into context, could you seriously generate a response of someone looking at your advert for 4 minutes in a newspaper? I don’t need to answer that for you, it is clear. For ASDA, they know that 4/5 people don’t shop in ASDA and that is OK. So why spend £150,000 on a single press release in a national newspaper when 4/5 people of the people still reading newspapers aren’t ever going to be interested in ASDA anyway?
The summary of Dom’s keynote speech was that brands and businesses need to take a step back and see what is happening in the world. It’s time to start creating more content that relates to your audience.
Cyber Security
The next session was all about cyber security and the steps you can take to protect yourself. You need to look no further than the recent headlines about how many companies have been hacked into last year with millions of customer details stolen; eBay, Sony, Moonpig and endless more including 273 million customer details stolen from Yahoo and 250,000 customer details stolen from Twitter.
Some interesting statistics announced around cybercrime included that it costs the UK economy over £6.8 billion per year and the global economy £238 billion annually. With 81% of large businesses having experienced security breaches in 2014. The cost of a typical breach is now at £1.15 million, up from £600,000 in the previous year.
Some of the most common attacks are due to very basic hacking just after Update Tuesday. Windows PCs are updated every Tuesday with security patches that have been identified to keep your system and data safe and secure, yet so many people either ignore the messages on their computers or simply turn off the automatic updates. This is mad! As part of the weekly update from Microsoft, the hackers use this information as a shopping list of exploits on computers around the world they can attempt to get access to. If your system isn’t up to date, then you could be at risk.
Moving onto more sophisticated attacks such as DDoS attacks, which stands for Distributed Denial of Service attacks, these can bring down websites with ease. To the point at which you can actually purchase an attack on the black market to target a specific website for a specific amount of time. Unlawful and illegal hacking is turning into an underground commercial business. DDoS attacks are actually quite simple;
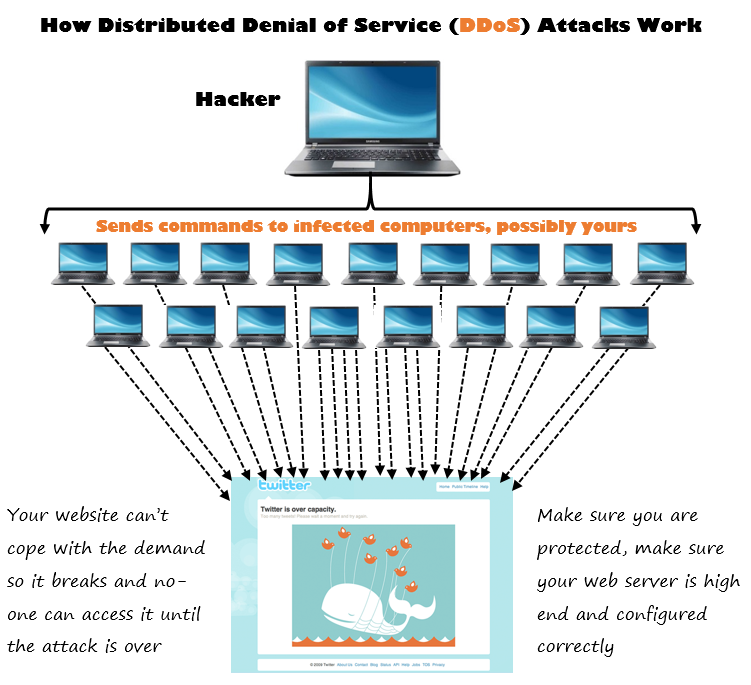
This method for DDoS are often using thousands, hundreds of thousands if not millions of computers from around the globe. For example, here you can see a short visualisation of a DDoS attack happening in real time on my personal blog a couple of years ago;
Have a read more about the full details if you are interested. The exact same thing happened to Mastercard, Visa and PayPal when they decided to stop sending funds through to the hacker group Anonymous. Whether you agree or disagree with this is another discussion all together and one that doesn’t have a simple answer. The important point here is that DDoS attacks are a real and present threat for businesses. While it is unlikely that you will encounter the wrath of some of the more prolific public hacking groups, the reality is that a lot of business websites for SMEs are hosted on cheap and nasty web servers that are poorly configured and have very little security built into them. Make sure your web server has the right protection in place to at least minimise the chances of DDoS attacks affecting you. The unfortunate reality is that if someone is determined enough to bring your website down, they will do. You can make it harder for this to happen though by having the right infrastructure in place for your website. Aren’t sure if your website and web server is protected? Then get in touch and we can review to check for vulnerabilities.
Moving away from hacking and looking at other types of data breaches now. Some of the most common data breaches often come in much simpler formats and often due to human error, aka. lack of awareness about threats. Threats including basic passwords on mobile and tablet devices to avoid automatic access to cloud based file storage systems for your company if a device is lot of stolen, to a deeper understanding of programming languages to avoid rookie mistakes.
Website vulnerabilities in particular happen for a number of reasons including unpatched software/content management systems/plugins, poor coding practices, poor server configuration, unencrypted data and more. Getting all of the above right is the absolute minimum businesses should be doing. Simply having a website built and not thinking about on-going updates is madness with how easy it is to exploit unloved websites. Every website should have regular and on-going maintenance to keep the website, content and data secure.
As of this year, there will be new EU Data Protection legislation that will be coming into force that businesses must adhere to. All of which is designed to move the current legislation into the digital age where customer data is collected at an alarming rate, often with very little visibility about what is being collected. This is likely to include full disclosure when data breaches happen so that customers are aware of what has happened. Far too often, businesses try and sweep large data breaches under the rug and hope that no-one will notice.
During the session, a live demonstration was given showing how easy it is for someone to steal your details – Even with my background, I was surprised at the level of things that can be done to steal personal details without you ever knowing what has happened. For example, simple things like clicking a link in an email can allow hackers to steal all of your saved login information in your browser. It really is that simple. Likewise, downloading a seemingly normal looking file from an untrusted source can result in a Key Logger being installed on your computer which will then be able to ‘read’ every single key you press, including your online bank account details and email passwords.
You may have heard about the infamous Stuxnet virus that swept the world almost by stealth last year. If you haven’t, you really need to read a few articles about this serious security threat; Wired, Business Insider, Wikipedia and what is even more worrying is that the source code for the virus is now publicly available on certain websites. As a quick overview if you haven’t come across Stuxnet before, the virus was designed specifically to find a physical controller located in power plants that controlled the heating/cooling of the nuclear material. As you can imagine, hacking into this and reporting an incorrect figure would lead to catastrophic results. This shows how sophisticated hacking has become. Some sources say that the virus was created by the US to target Iran’s nuclear facilities – how true this is, I don’t know. Other notable viruses including Duqu and Flame again highlight the level of sophistication that is happening right now.
Other common hacking attacks include the likes of SQL Injection attacks and Cross Site Scripting (XSS) attacks. Have a read up on these, again hugely important issues to be aware of and protect yourself against. Inexperienced and junior people working in digital are often oblivious to all of this type of information and most importantly how to protect against it. Always work with a company and people who are professional and have a very deep understanding of the industry they are working on. Remember the quote “If you think it’s expensive to hire a professional to do the job, wait until you hire an amateur”.
Now can you see why it is important to keep your systems, website and servers secure? Good, I’m glad the message has been received. If you don’t know what to do next, then get in touch and let’s have a chat.
Online Retail Panel

Next up was the panel that I was part of alongside three other digital agency owners in Manchester and London along with the Head of Online Retail for Iceland Foods, Andy Thompson. The session took a rather interesting turn to talk around a lot of digital topics about business growth through online retail, internal communication challenges and solutions along with some blindingly obvious opportunities for large brands to improve their sales online. The talks should be going online once they have been edited which you can look forward to watching, so for the meantime, here is a quick summary of the whole event and more information can also be found on the website;

Digital Marketing, SEO and the Internet of Things
The last few sessions of the day are combined within this section. We heard from many different speakers and panellists in the final sessions with lots of great tips for businesses. One key message that is extremely relevant for the SME market is that you simply can’t have social media accounts without creative content. You need to be creating your own content and sharing this socially along with utilising other great content around the web to fuel your social media channels.
The Tales of Things by Oxfam
Oxfam was involved in a very interesting project with the University of Salford titled The Tales of Things. Oxfam have invested £1.4 million over the past 3 years with the aim of revolutionising business systems and processes through the use of digital technologies. The Tales of Things project was a very interesting one and one which I believe we will start to see more of over the next few years.
The idea was around selling donated products that also have a QR code attached to them. Customers looking at the item would then scan the QR code to listen to a short story from the person who donated the item. Oxfam found that this actually increased sales by 57% in the Manchester shop. They then extended this into Selfridges in London where celebrities donated items with the same concept behind. Within 14 weeks, they had this technology applied in 10 Manchester shops. This is ultimately a historical archive for objects that are traded, thus turning an object into something more than an object as it has a story behind it.
Personally I hate QR codes with a passion due to the way that they are misused in 99% of circumstances by businesses. Although in this instance with Oxfam, this is a really great way to bring things to live and genuinely adds value to the product being purchased and the customer experience.
This project has been on-going for a few years now so have a good read about the finer details over at the BBC, Oxfam and Tales of Things.
Cool Tech
Where would we be without a blog post talking about some cool technology that is on the horizon? Here is a really cool digital air hockey game that Tom Cheesewright and I played (which I think I won, Tom may disagree, not that I’m competitive in any way! );

Image courtesy of Aleksej Heinze
And this was even more amazing, a 3D holographic projection (apologies for the poor quality, it was taken on my smartphone);
Summary of Event
Overall, the event was excellent with lots of great tips and advice to take away and implement. I’m sure there are a lot of questions about what you need to be focusing on in your business after the security discussions and digital marketing opportunities discussed above. Get in touch and we can talk things through with you to see how we can support the growth of your business.
Keep an eye out for next year’s event






















